Endpoint Encryption Tech Code Generator
.

Endpoint encryption tech code generator. If your product is successful, someone will make a key generator in a matter of days from release. Encrypted Email, Encrypted file. DES was considered insecure as early as 1977, and documents leaked in the 13 Snowden leak shows that it was in fact.
NSA lobbied for a key size of 48 bits. Source code can also be compiled with VS08, VS08 Express Edition and VS10 Express Edition, although current project and makefile are not fully compatible anymore. Hypervisor-protected Code Integrity (HVCI).
The JHipster Registry has three main purposes:. Windows X-server based on the xorg git sources (like xming or cygwin's xwin), but compiled with Visual C++ 12 Express Edition. OpenKeychain is a leading choice for tech-savvy Android users looking to encrypt email and messages.
AES was created as an alternative to the Data Encryption Standard (DES), because it became vulnerable to brute-force attacks. The new random generator is essentially a port of the default random generator from the OpenSSL FIPS 2.0 object module. 19- IEEE Access 影响指数是 4.640。 36%的科学家预测 IEEE Access -21影响指数将在此 4.5 ~ 5.0 范围内。 IEEE Access的最新影响指数分区 為1区。.
These IP solutions can be used to accelerate design development and reduce project. The JHipster Registry is a runtime application, provided by the JHipster team. Allison Mankin and Michael Tuexen DCCP:.
Tech Tech Buzz By :. 7,616 Code Commits Make Your Projects Come To Life With the tools we provide, developers on SourceForge create powerful software in over 502,000 open source projects;. Advanced encryption and strict no-log policy Avira is one of the most trusted software brands in the world and has a 30-year history of ensuring privacy and security for users worldwide.
Detects the Murmur service (server for the Mumble voice communication client) versions 1.2.X. Windows users who need onboard device encryption Microsoft's BitLocker, available on business editions of the OS and server software, is the name given to. Some of its new features are:.
Advanced Encryption Standard as specified by NIST in FIPS 197.Also known as the Rijndael algorithm by Joan Daemen and Vincent Rijmen, AES is a 128-bit block cipher supporting keys of 128, 192, and 256 bits. If you have any feedback please go to the Site Feedback and FAQ page. Encrypt sensitive data before it is shared over untrusted networks (ex.
The key to a good encryption strategy is using strong encryption and proper key management. Microsoft BitLocker Free Best suited for:. A pair of QKD systems has a list price of $,000.26.
Queries for the multicast path from a source to a destination host. The SunJSSE provider uses JCA exclusively for all of its cryptographic operations and can automatically take advantage of JCE features and. Help Desk KB Team.
The company currently has employees and three business units (scientific instrumentation, random number generator, network encryption). Calculate the solution for a scrambled cube puzzle in only steps. Encryption - Encryption is a very generic term and there are many ways to encrypt data.
Obfuscating the algorithm or hiding an encryption key within your software is really out of the question if you are serious about controlling licensing. The widely used DES encryption algorithm was originally planned by IBM to have a key size of 128 bits;. When enabled and configured, Windows 10 can start the Hyper-V virtualization-based security services.
Based on the OpenPGP standard, OpenKeychain itself is not a messaging or email app but instead integrates with popular Android apps like K-9 Mail and Conversations to make OpenPGP encryption conveniently available to mobile users. According to Bruce Schneier, “the math is good, but math has no agency. Talent Recruit tech talent & build your employer brand;.
. It is a hybrid deterministic random bit generator using an AES-CTR bit stream and which seeds and reseeds itself automatically using trusted system entropy sources. With a strict no-log policy and state-of-the-art end-to-end encryption, you can be sure that your data stays completely private.
DoIT Help Desk, DoIT Tech Store:. Encryption type —The encryption type length —The RSA key length or DH group number Recommended Action Configure the ASA or external application to use an RSA key that is at least 48 bits, or to configure a DH group that is not 1, 2, or 5. The end compromise were a key size of 64 bits, 8 of which were parity bits, to make an effective key security parameter of 56 bits.
Resolved compatibility issues with PGP Whole Drive Encryption, SafeBoot, and PointSec encryption software. This includes applications such as VPNs, and therefore, makes it even easier to break. Like the JHipster generator, it is an Open Source, Apache 2-licensed application, and its source code is available on GitHub under the JHipster organization at jhipster/jhipster-registry.
We host over 2.1 million registered users. Unfortunately, the researchers found that only a few prime numbers are commonly used for 1024-bit encryption. Visita la entrada para saber más.
Code has agency, and the code has been subverted”. Hypervisor-protected Code Integrity is a feature of Device Guard that ensures only drivers, executables, and DLLs that comply with the Device Guard Code Integrity policy are allowed to run. Intel FPGA and its Intellectual Property partners offer a large selection of off-the-shelf IP cores and reference designs optimized for Intel FPGA, CPLD, and ASIC devices.
The Java Cryptography Architecture (JCA) is a set of packages that provides a framework and implementations for encryption, key generation and key agreement, and message authentication code (MAC) algorithms. Enhanced security for Win 9x operating systems. SPSS update license code existing SPSS installation IBM mac windows statistics software 17 SPSS17 trial file spss22 Suggest keywords:.
K527 ESET AV Remover—List of removable applications and instructions to run the tool. IBM Developer More than 100 open source projects, a library of knowledge resources, and developer advocates ready to help. The JHipster Registry Overview.
Apasionado Tecnologico en las areas de Setup, Unattended and Deployment de Windows. Companies need to implement and manage encryption correctly. Queries an MSRPC endpoint mapper for a list of mapped services and displays the gathered information.
Service Name and Transport Protocol Port Number Registry Last Updated Expert(s) TCP/UDP:. CIOL Writers A new malware with roots in China that has infected over 250 million computers worldwide was recently discovered by Check Point threat intelligence and research teams. Set up the scramble pattern, press the Solve button and follow the instructions.
143 151 Comment Suggest a new document. Jesús Octavio Rodríguez de Santiago. Because the encryption caused so many bit-level changes to the drive the software made fresh backups of everything and deleted old backups to make room for the new corrupted files.
Developed by the National Institute of Standards and Technology (NIST), Advanced Encryption Standard (AES) is a block cipher that provides fast, strong, and secure encryption of classified data. Eliot Lear, Allison Mankin, Markku Kojo, Kumiko Ono, Martin Stiemerling, Lars Eggert, Alexey Melnikov, Wes Eddy, Alexander Zimmermann, Brian Trammell, and Jana Iyengar SCTP:. Eddie Kohler and Yoshifumi Nishida Reference RFC6335 Note Service.

How To Install Openfaas With Docker Swarm On Ubuntu 16 04 Digitalocean

15 Free Mobile Encryption Apps To Protect Your Digital Privacy Digital Guardian
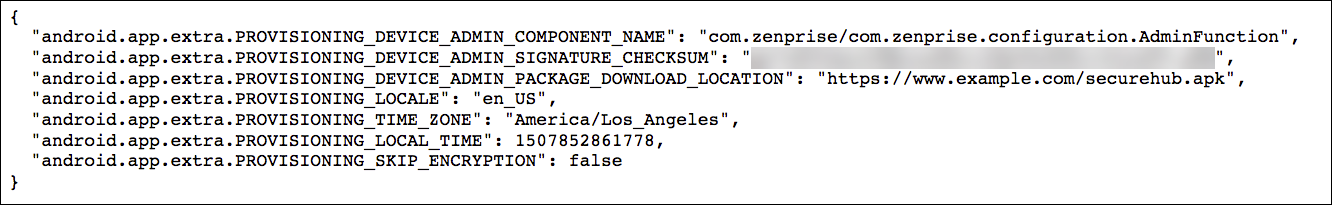
Android Enterprise
Endpoint Encryption Tech Code Generator のギャラリー
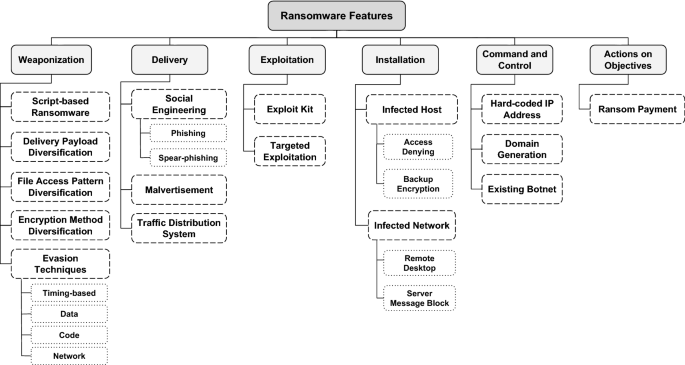
A Cyber Kill Chain Based Taxonomy Of Crypto Ransomware Features Springerlink
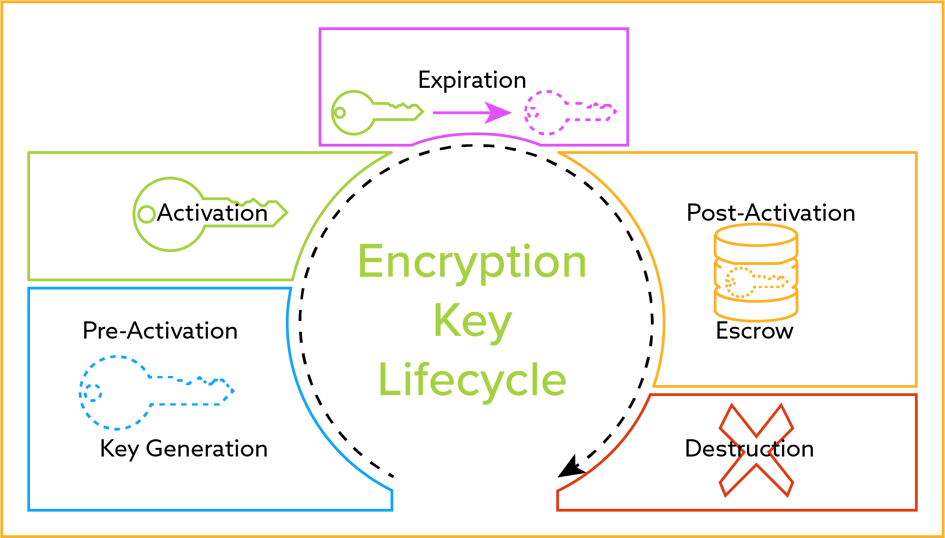
The Definitive Guide To Mongodb Encryption And Key Management
Prisma Horizontal Scaling A Practical Guide By Nicola Molinari Commercetools Tech
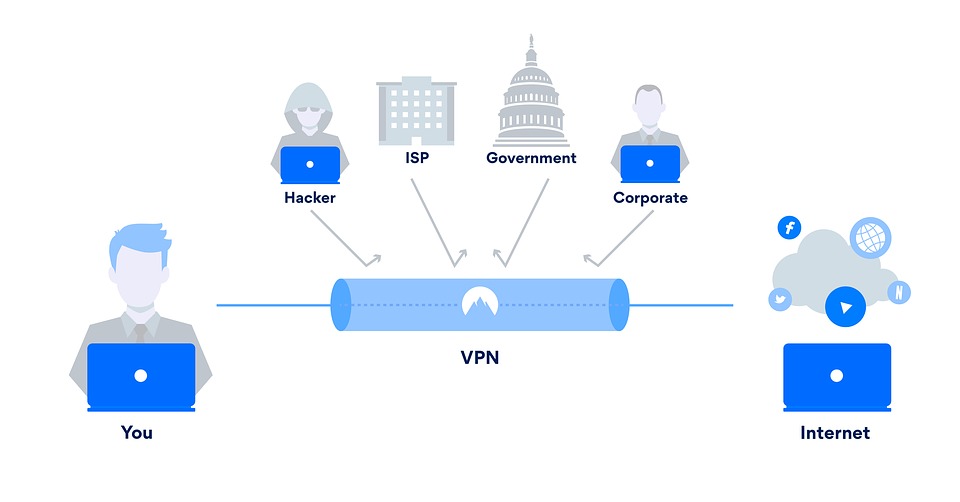
How Do Vpn Encryption Protocols Work At T Cybersecurity

Double Key Encryption Dke Microsoft 365 Compliance Microsoft Docs

Arm Mbed Tls In Microsoft Visual Studio 15 Knowledge Base Mbed Tls Previously Polarssl

Tech And Dev Wordpress Encryption Tools Generator Plugin

Best Encryption Software For Business In Bitlocker Filevault Guardium And More Zdnet

Best Encryption Software In 360quadrants
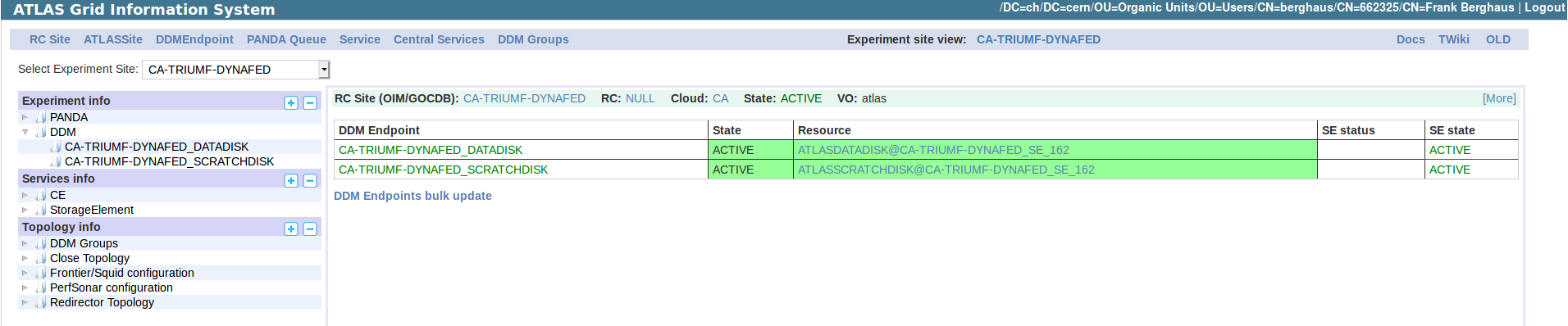
24th International Conference On Computing In High Energy Nuclear Physics 4 8 November 19 Indico

Sophos Endpoint Protection Intercept X With Edr
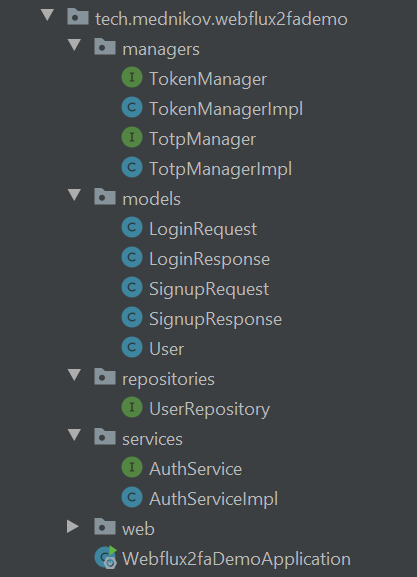
Two Factor Authentication In Spring Webflux Rest Api Dzone Security

Types Of Encryption 5 Encryption Algorithms How To Choose The Right One Security Boulevard

Obfuscation Code An Overview Sciencedirect Topics

Types Of Two Factor Authentication Pros And Cons Sms Authenticator Apps Yubikey Kaspersky Official Blog

Swedish Windows Security User Group

15 Free Mobile Encryption Apps To Protect Your Digital Privacy Digital Guardian
Ec Europa Eu Research Participants Documents Downloadpublic Documentids e5b5679bfe Appid Ppgms
How To Remove Disk Encryption In Mcafee Technical Skills
How To Remove Disk Encryption In Mcafee Technical Skills

Double Key Encryption Dke Microsoft 365 Compliance Microsoft Docs

Multi Environment Ci Cd Pipelines With Aws Codepipeline And Open Source Tools Aws Open Source Blog

Encrypted Api Testing Using Jmeter Rapidvalue

Obfuscation Code An Overview Sciencedirect Topics

Codestencil The Ultimate Code Generator Home

Enterprise Security Model Lastpass

Transport Layer Security Wikipedia

Mcafee Data Loss Prevention Release Code Keygen

How To Authorize Eetech Detech With The Code Of The Day How To S

3 Key Configuration Challenges For Kubernetes Monitoring With Prometheus The New Stack
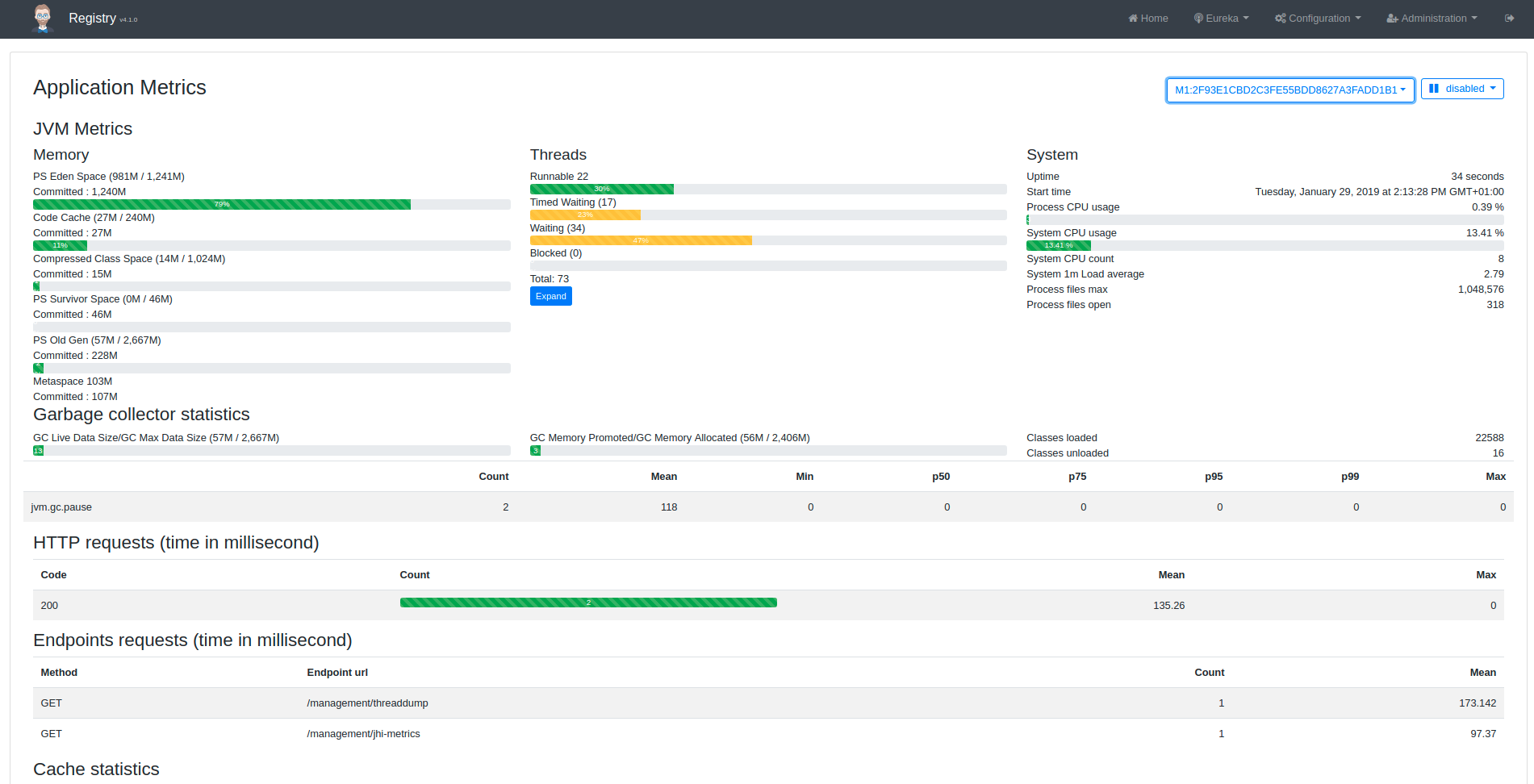
Jhipster Registry

The Definitive Guide To Mongodb Encryption And Key Management
Q Tbn 3aand9gcqtn0ybz9 oqo Bldjeu9ktsq8czjmpnvaxtvvfsw0dppj6 O Usqp Cau
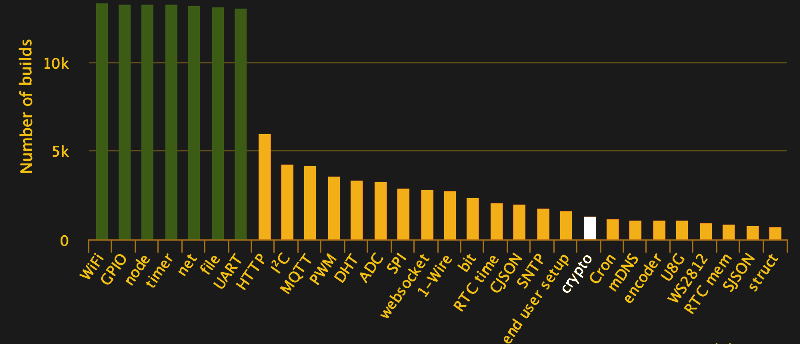
Practical Iot Cryptography On The Espressif Esp66 Hackaday

Introducing Cryptokit Raywenderlich Com

Hash Code Generators And Cryptography Tools My Tec Bits

Data Privacy In The Us And Privacy Shield

Data Privacy In The Us And Privacy Shield
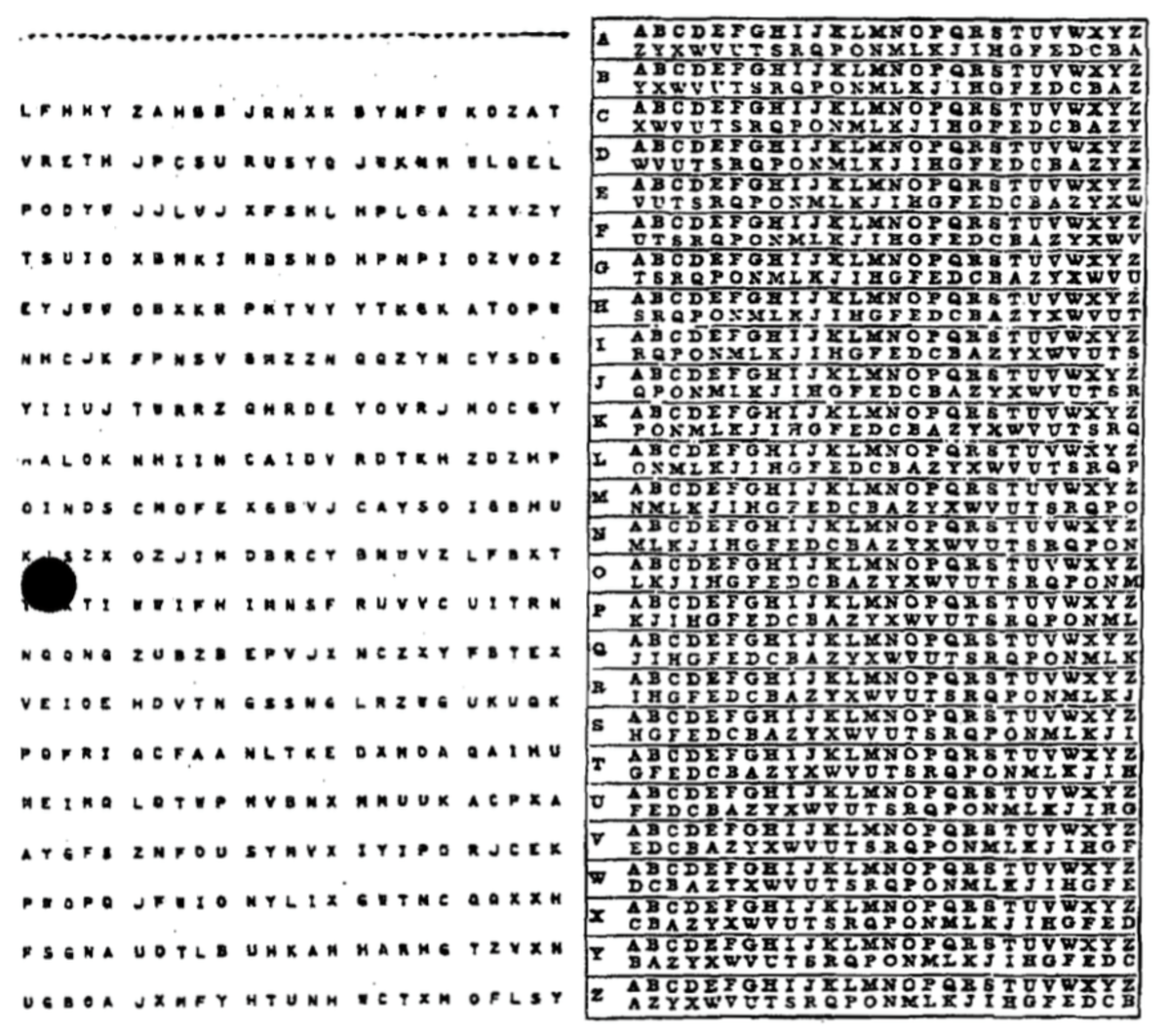
One Time Pad Wikipedia

Types Of Two Factor Authentication Pros And Cons Sms Authenticator Apps Yubikey Kaspersky Official Blog
Undressing The Revil Trustwave

How To Authorize Eetech Detech With The Code Of The Day How To S
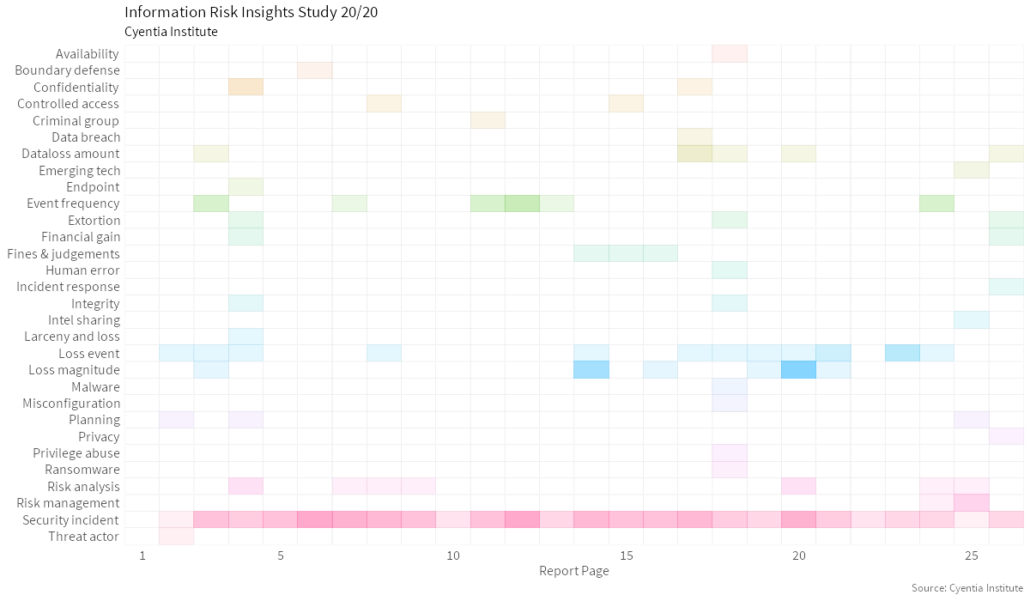
Gartner Cloud Solutions Architect

Diffie Hellman Key Exchange Vs Rsa Encryption Venafi
Faculty Nps Edu Dedennin Publications Denning Cryptographydatasecurity Pdf

How To Create A Strong Password And Beat The Hackers Avast

Automated Cryptocode Generator Is Helping Secure The Web

Psn Code Generator Apk Download
Jbake

Solved Mcafee Support Community Unable To Locate Tech Code Generator Mentioned In Mcafee Support Community
Android Enterprise
How To Remove Disk Encryption In Mcafee Technical Skills

Aws Security Webinar The Key To Effective Cloud Encryption

Create Your Own Connector Matillion Etl Documentation

Solved Mcafee Support Community Unable To Locate Tech Code Generator Mentioned In Mcafee Support Community
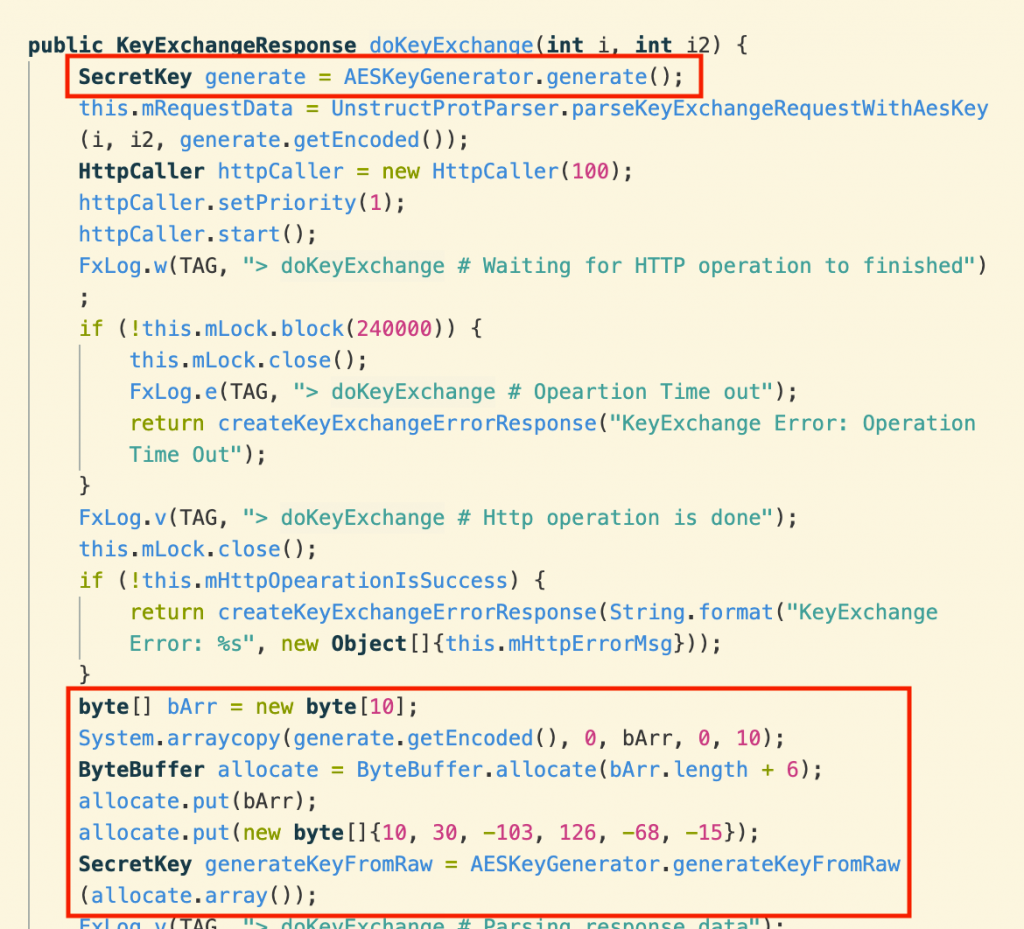
Stalking Stalkerware A Deep Dive Into Flexispy Official Juniper Networks Blogs
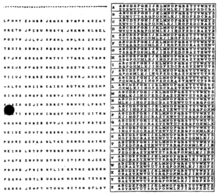
One Time Pad Wikipedia

Mcafee Center Stage Mde Disaster Recovery Youtube
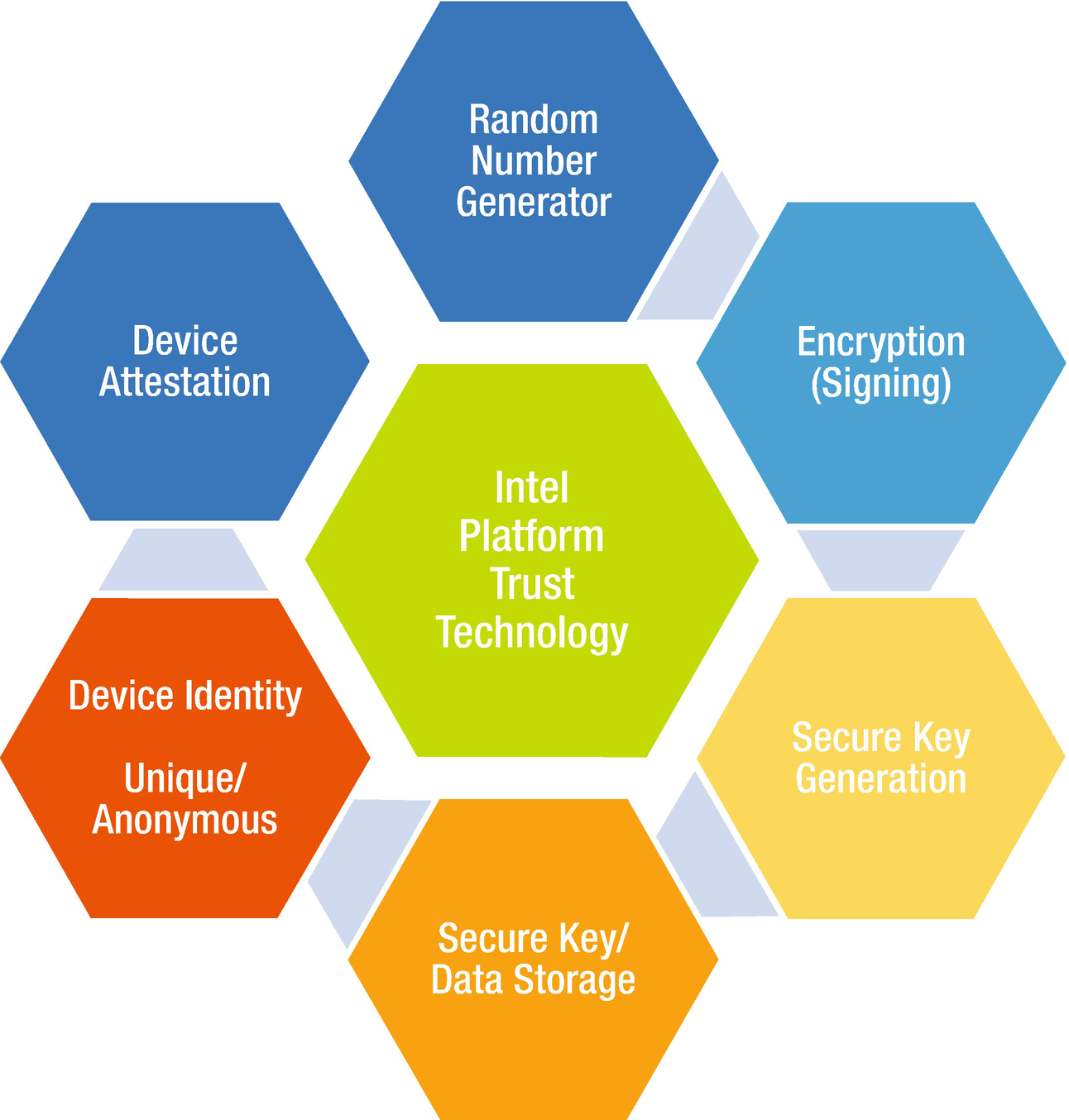
Base Platform Security Hardware Building Blocks Springerlink

Best Encryption Software For Business In Bitlocker Filevault Guardium And More Zdnet

Digital Ai Encryption Key Management Data Protection Digital Ai
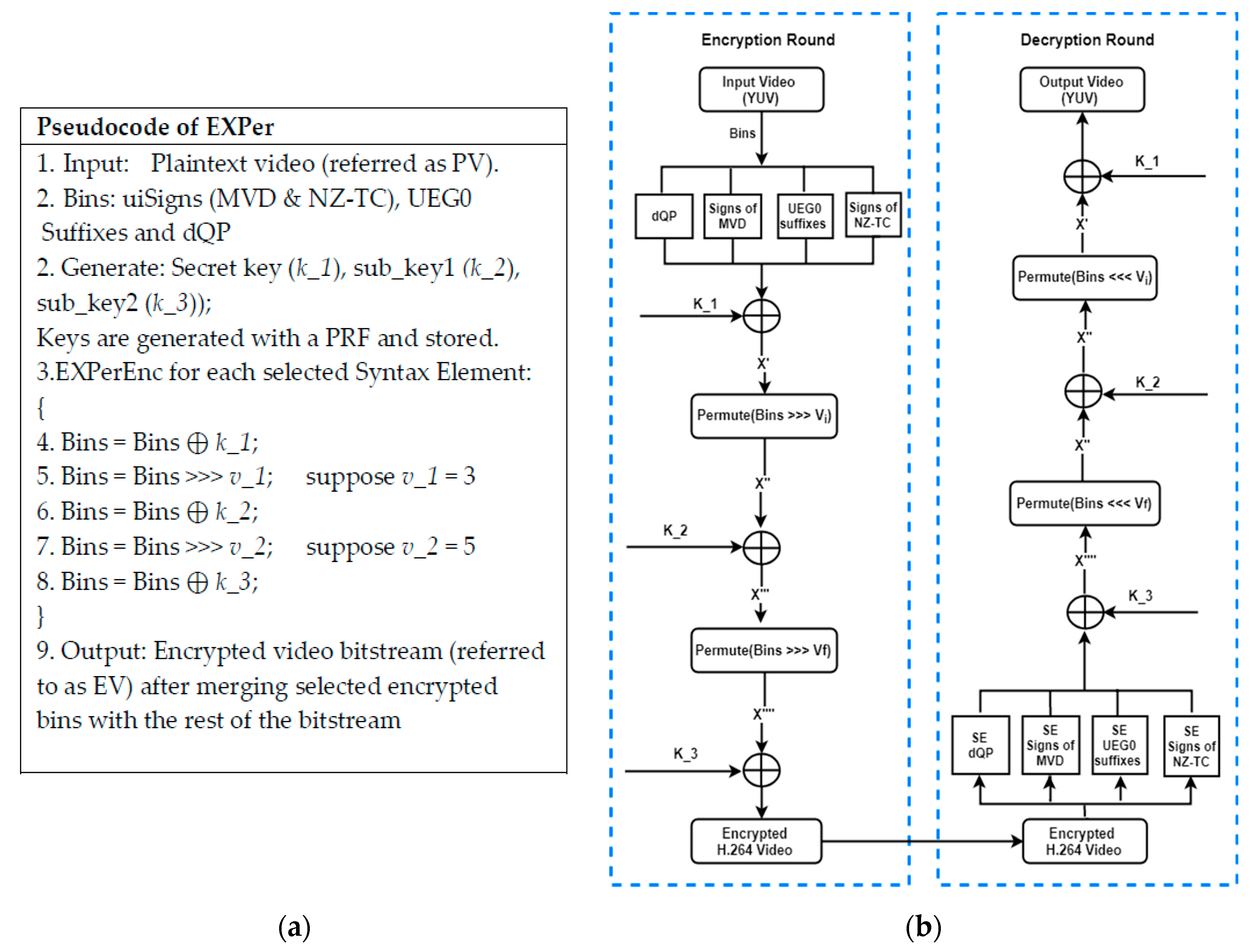
Sensors Free Full Text Lightweight Cipher For H 264 Videos In The Internet Of Multimedia Things With Encryption Space Ratio Diagnostics Html

Introducing Cryptokit Raywenderlich Com
2
Q Tbn 3aand9gcqaxd4ppik0 8u38n22uvxcr4i0 Eoodqpnxw Usqp Cau

Mcafee Drive Encryption Manuel Boot And Decryption Process With Eetech Youtube
1

Sophos Endpoint Protection Intercept X With Edr

Solved Mcafee Support Community Unable To Locate Tech Code Generator Mentioned In Mcafee Support Community

Best Encryption Software For Business In Bitlocker Filevault Guardium And More Zdnet

Sovled Mcafee Removal Tool Uninstaller Up Running Technologies Tech How To S

Multi Environment Ci Cd Pipelines With Aws Codepipeline And Open Source Tools Aws Open Source Blog
How To Remove Disk Encryption In Mcafee Technical Skills

How Nsa Weakens Encryption To Access Internet Traffic New Scientist
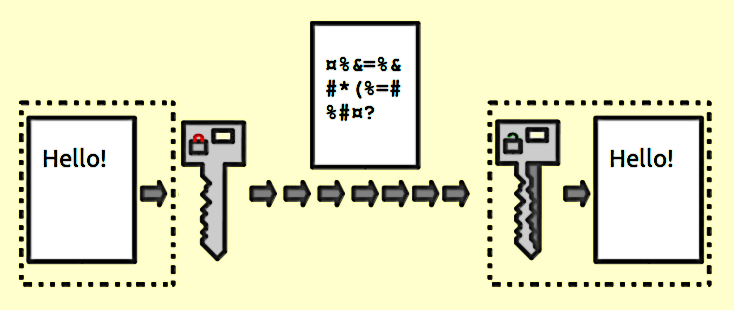
The Most Popular Free Encryption Software Tools To Protect Your Data
Common Encryption Types Protocols And Algorithms Explained
How To Remove Disk Encryption In Mcafee Technical Skills
2 Encryption And Its Applications Decrypting The Encryption Debate A Framework For Decision Makers The National Academies Press

Video Embedding Or Streaming Capabilities Zesty Io Documentation

Protect Your Company Learn How Cyber Criminals Gain Access
.jpg)
Mcafee Support Community Need Tech Code Generator Mcafee Support Community

Epm Saas Technical Datasheet Cyberark Docs
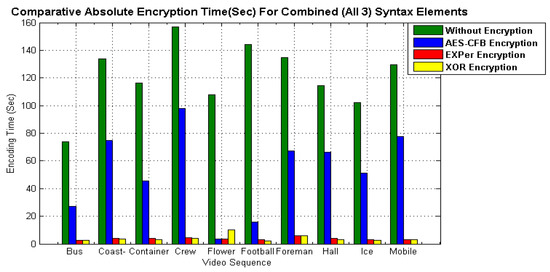
Sensors Free Full Text Lightweight Cipher For H 264 Videos In The Internet Of Multimedia Things With Encryption Space Ratio Diagnostics Html
Techcode Com Siteglimpse

Solved Mcafee Support Community Unable To Locate Tech Code Generator Mentioned In Mcafee Support Community
Encryption Vs Tokenization Vs Whatever What You Need To Know Techbeacon
7xdcykxjrhhaxm

Types Of Encryption 5 Encryption Algorithms How To Choose The Right One Security Boulevard
The Most Popular Free Encryption Software Tools To Protect Your Data

Best Encryption Software In 360quadrants

A Deep Dive Into Phobos Ransomware Malwarebytes Labs Malwarebytes Labs

Mcafee Data Loss Prevention Release Code Keygen

Aws Security Webinar The Key To Effective Cloud Encryption

A Deep Dive Into Phobos Ransomware Malwarebytes Labs Malwarebytes Labs

Random Code Generator Create Strong Security Keys Steemit

How To Authorize Eetech Detech With The Code Of The Day How To S

Evolution Of Gandcrab Ransomware Acronis

Bmn Wtfet11uom

Tech And Dev Wordpress Encryption Tools Generator Plugin




